Scoping CUI for CMMC Level 2 Certification
Introduction
One of the most important steps in achieving CMMC Level 2 certification is correctly scoping your Controlled Unclassified Information (CUI) environment. Defining scope properly not only reduces complexity during the assessment process—whether you’re preparing for a self-assessment or a C3PAO-led audit—but also ensures smoother handling of CUI in day-to-day operations.
In this post, we’ll walk through what scoping means, why it’s required, and how organizations can confidently establish their assessment boundaries.
CMMC and the Role of Scoping
The Cybersecurity Maturity Model Certification (CMMC) program became enforceable through 32 CFR Part 170 in December 2024. Within this regulation, 170.19(a) makes it clear:
“The CMMC Assessment Scope must be specified prior to assessment in accordance with the requirements of this section. The CMMC Assessment Scope is the set of all assets in the OSA’s environment that will be assessed against CMMC security requirements.”
Subsection 170.19(c) further states that prior to performing a Level 2 assessment—whether self-led or through a C3PAO—an Organization Seeking Assessment (OSA) must define its scope.
To do this, the CMMC Level 2 Scoping Guide (v2.13) is your primary reference. It introduces five categories for classifying assets within the CUI environment:
CUI Assets
Security Protection Assets (SPA)
Contractor Risk-Managed Assets
Specialized Assets
Out-of-Scope Assets
Asset Classification and Documentation
The Scoping Guide requires OSAs to “document asset treatment in the System Security Plan (SSP).”
In practice, this means:
Identifying all assets within the system boundary
Categorizing each asset by type
Explaining how protections are applied
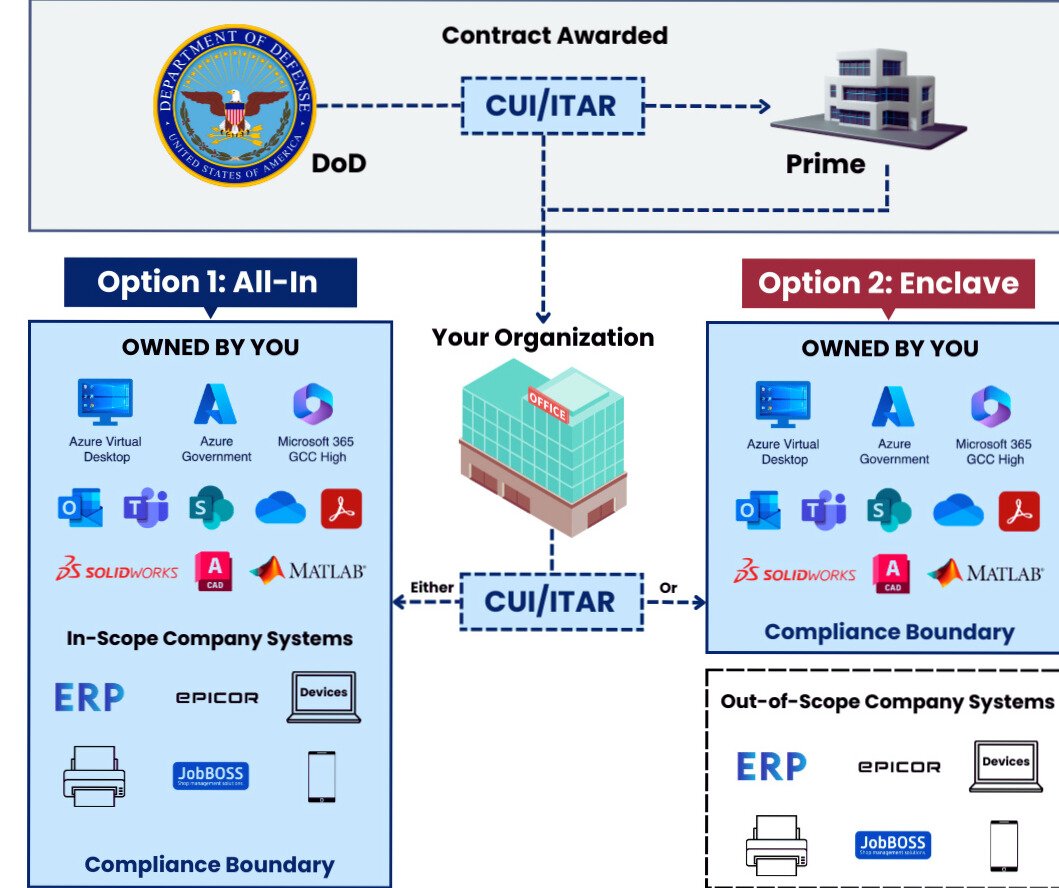
Supporting diagrams such as CUI data flow maps and network diagrams provide valuable clarity to assessors and help demonstrate that scoping decisions are both intentional and justified.
At its core, asset classification answers three simple questions:
What do you have? (Identify all relevant assets)
What does it do? (Define each asset’s role)
Where is it? (Explain how and where the asset is secured)
Example CUI Flow Diagram
Step 1: What Do You Have?
Begin with an inventory of every asset that touches CUI. Ask questions such as:
What systems, users, and facilities are involved as CUI enters, flows through, and exits your organization?
Do you use an External Service Provider (ESP)—such as a managed service provider (MSP) or cloud service provider (CSP)? What role do they play in handling CUI?
Step 2: What Does It Do?
Next, classify each asset based on its function within the CUI environment:
If it processes, stores, or transmits CUI, it’s a CUI Asset.
If it provides a security function, such as VPNs, SIEMs, or access control systems, it’s a Security Protection Asset.
People (consultants, admins), facilities (data centers, SOCs), and service providers should also be included in this review.
A CUI-specific data flow diagram is especially useful when multiple parties are involved in handling sensitive data.
Step 3: Where Is It?
Finally, consider the protections in place:
Physical protections: Is the asset in a secured server room or restricted-access area?
Logical protections: Is it segmented from other systems with strict access controls?
A network diagram showing how assets are segmented, where access controls apply, and how protections are layered will strengthen your documentation and help assessors clearly understand the environment.
CUI Scoping Preparation Checklist
Track how CUI enters, moves through, and exits your environment.
Build a complete inventory of systems, users, devices, cloud environments, and facilities tied to CUI.
Categorize each asset using the five CMMC asset types.
Create a CUI-specific data flow diagram to show how data moves between assets and providers.
Develop a network diagram highlighting segmentation, boundaries, and controls.
Document which assets are in scope and explain why.
Update your SSP with all diagrams and scoping details to support assessor review.
Next Steps and How Maverc Technologies Helps
Once your CUI scope is defined and documented, ensure that your System Security Plan (SSP) contains all related diagrams and rationale. A well-prepared SSP is invaluable during an assessment and helps avoid confusion or misinterpretation by the assessment team.
At Maverc Technologies, we guide organizations through every step of the CMMC journey—from scoping and asset classification to assessment readiness. Our experience across cybersecurity frameworks and DoD requirements allows us to provide tailored support to both small contractors and large primes.
If your team needs help defining scope, categorizing assets, or preparing documentation, Maverc can help ensure you’re fully prepared for CMMC Level 2 certification.
Ready to get your CUI scoping right? Contact Maverc Technologies today to begin your compliance journey.